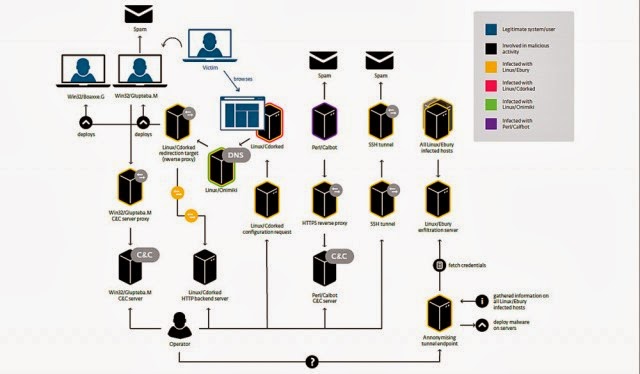
Researchers have documented an ongoing criminal operation infecting more than 10,000 Unix and Linux servers with malware that sends spam and redirects end users to malicious Web pages.
Windigo, as the attack campaign has been dubbed, has been active since 2011 and has compromised systems belonging to the Linux Foundation's kernel.org and the developers of the cPanel Web hosting control panel, according to a detailed report published Tuesday by researchers from antivirus provider Eset. During its 36-month run, Windigo has compromised more than 25,000 servers with robust malware that sends more than 35 million spam messages a day and exposes Windows-based Web visitors to drive-by malware attacks. It also feeds people running any type of computer banner ads for porn services.
The Eset researchers, who have been instrumental in uncovering similar campaigns compromising large numbers of servers running the nginx, Lighttpd, and Apache Web servers, said the latest campaign has the potential to inflict significant harm on the Internet at large. They explained:
The number of systems affected by Operation Windigo might seem small when compared with recent malware outbreaks where millions of desktops are infected. It is important to keep in mind that, in this case, each infected system is a server. These usually offer services to numerous users and are equipped with far more resources in terms of bandwidth, storage and computation power than normal personal computers. A denial of service attack or a spam-sending operation using one thousand servers is going to be far more effective than the same operation performed with the same number of desktop computers.For more....
No comments:
Post a Comment